Interconnected Tech Notes - June 28, 2017
 Wednesday, June 28, 2017 at 9:31AM
Wednesday, June 28, 2017 at 9:31AM Hello all,
It's been a little quiet here on the Blog. We've been busy helping clients make their I/T work well for them, and haven't been doing much writing!
A couple of recent things prompt this Tech Note:
1. The Petya ransomware attack yesterday. About this, from the folks at Symantec:
A new strain of ransomware has appeared in multiple countries. On June 27, 2017, Petya ransomware emerged and began spreading itself to large organizations across Europe. This ransomware uses what is called the Eternal Blue exploit in Windows computers.
Norton is already protecting you against the Petya attacks that use the Eternal Blue exploit. This is why we have Norton Security on all computers.
Protecting against this type of attack is also why we're in the process of re-evaluating our position on and recommendations for network firewalls. Stay tuned for more on that!
2. Jungle Disk is updating again.
Many clients have contacted us about a recent prompt from Jungle Disk (the backup program on which we and most of our clients depend) to update to a new version.
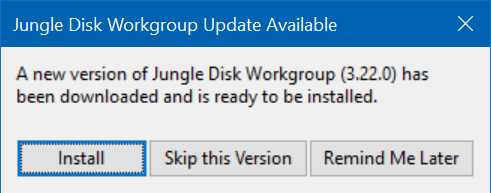
Generally speaking, this update should be done as soon as possible. The servers on which our backups are stored are getting an important security update which will require the new version. While they haven't announced precisely when this will happen, getting the Jungle Disk program updated now will avoid any difficulties when that happens.
The update takes just a minute or two, depending on the speed of your machine. If you decide to try this update yourself, please pay close attention to the end of the process, and make sure that it says it completed succesfully. If you're not sure, don't want to this yourself, or if the update fails, you know where to reach us!
With these, as with all other technology matters, please contact us if you have questions or need assistance!